People, Technology, and Process: Stopping a DocuSign Impersonation Without Disruption
Industry: Professional Services
Client Size: SMB
Engagement: Managed IT + Email Security + Security Awareness Training (SAT)
PremierePC Services in Place: Inbound Email Security & Compliance platform (quarantine + analytics), SAT platform with phishing simulations and employee scoring
Trigger: User-reported “DocuSign emails blocked for everyone” with a screenshot claiming action required
Blocked Threat: DocuSign impersonation phishing
Outcome: 0 false positives, no disruption, protections preserved
Executive Summary
A user at a professional services firm submitted a helpdesk ticket claiming PremierePC was “blocking DocuSign emails for everyone.” They requested an allow-list rule to “fix” the issue. But our investigation told a very different story.
Over a 14-day trace, we found no legitimate DocuSign messages blocked. Instead, we uncovered phishing emails impersonating DocuSign—correctly quarantined by our filters using multiple threat signals.
This case illustrates why smart security isn’t just about tools—it’s about combining people, technology, and process.
- Technology did its job: the inbound filter flagged multi‑signal risk and quarantined the messages.
- Process matters: before adding bypass rules, the right step is to engage IT to verify and analyze.
- People need reinforcement: despite a passing SAT score, the user did not consult the quarantine reasons panel or escalate for validation—both provided in our tools and onboarding.
We used this as a coaching opportunity, tuned user guidance, and left protections intact—avoiding unnecessary allow‑listing that would have created risk.
Environment & Controls
- Inbound email security with quarantine, icon‑based scoring, and reason codes (why a message was held).
- SAT platform with ongoing micro‑trainings, simulated phishing, and employee security scoring.
- Helpdesk workflow for suspected false positives (trace + review before allow‑lists).
What Happened
- A helpdesk ticket was filed: “DocuSign emails are being blocked for everyone.”
- A screenshot was provided showing quarantined messages.
- The client requested a global allow-rule for DocuSign.
Our team traced inbound messages for two weeks:
- Result: No real DocuSign messages were blocked.
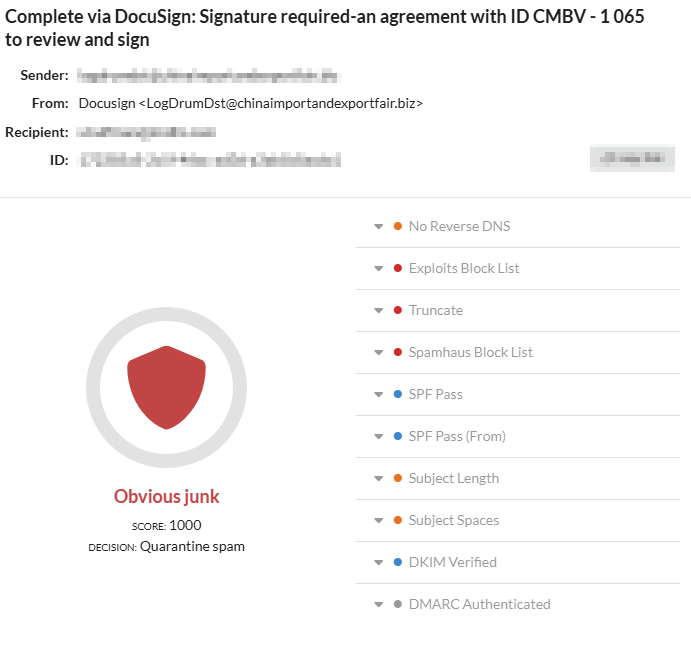
- Finding: Phishing messages were flagged and quarantined for valid reasons:
- No reverse DNS
- Blocklisted IPs
- Suspicious subjects
- Spoofed sender domains
We explained the results to the client, preserved all security policies, and used the event as a coaching opportunity.
Why It Worked
Technology
Our email security platform scored each email using multiple risk signals and explained the quarantine reason in plain language.
People
Users had access to quarantine digests, reports, and escalation workflows—without needing to act blindly.
Process
Rather than approve a risky bypass, our process required verification. The client paused, checked with us, and avoided an unsafe change.
Outcome: The phishing attempt was contained without mail flow disruption; no legitimate DocuSign traffic was impacted.
Where It Broke Down (People & Process)
- The user passed their SAT training but skipped the quarantine explanation.
- They requested a global bypass before validation—a risky move.
- Takeaway: Cybersecurity training must turn into habits, not just scores.
Lesson: Training scores are not the goal; behavior at the moment of decision is. Pair training with simple, repeatable steps users follow every time they suspect a block.
Our Playbook: When You Think an Email Was Blocked
- Open the quarantine email or portal.
- Read the reason codes (e.g., blocklist hit, bad domain).
- Check the actual sender domain, not just the display name.
- If unsure, forward to PremierePC or use the built-in “Report Phish” button.
- Don’t request allow-listing until a technician confirms a false positive.
Outcome
- Zero legitimate DocuSign messages blocked during the review window.
- 100% of suspicious messages identified were phishing impersonations correctly quarantined.
- 1 User coaching session delivered and documented; follow‑up materials added to SAT reminders.
- 0 security policy changes needed. No policy erosion: Avoided risky allow‑listing.
Recommendations for the Client
- Adopt a “verify‑before‑bypass” workflow company-wide; route suspected misses to PremierePC first.
- Reinforce user steps with 1-minute visual refresher on how to review quarantined emails (screenshots of quarantine reasons + how to escalate).
- Schedule phishing simulations mimicking e-signature platforms like DocuSign and Adobe Sign
- Quarterly review of allow‑lists and transport rules to remove legacy exceptions.
- Manager dashboards in SAT to coach outliers even if their score is “passing.”
People + Technology + Process: How PremierePC Brings Them Together
- Technology: Managed inbound email security with clear quarantine analytics and policy enforcement.
- People: SAT with micro‑trainings, simulations, and employee scoring to build reflexes.
- Process: A defined false‑positive workflow (trace → validate → decide) that prevents knee‑jerk allow‑lists and preserves security posture.
We help small businesses make security simple, repeatable, and calm.
At‑a‑Glance
- 0 legitimate DocuSign blocks in 14‑day trace
- 100% of quarantined examples were brand impersonation
- 1 unified workflow: verify → validate → decide
How PremierePC Helps You Stay Safe
- Managed Email Security: Clear quarantine reports, analytics, and filtering rules.
- Security Awareness Training: Ongoing micro-trainings and phishing simulations.
- Expert-Led Process: A smart workflow that validates messages before risky changes are made.
